Your business, assets and data are vulnerable.
Mobile Application ecosystem has grown every year and vulnerabilities, security flaws and malicious users with it. Mobile Apps manipulate and use sensitive data. This affects your customers and your business. Protect both by securing your Mobile App: now you can analyze it and fix the vulnerabilities.

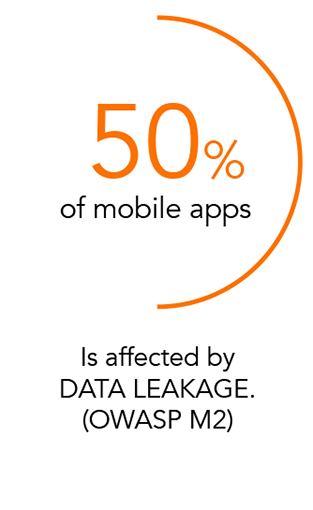



STANDARDS COMPLIANCE
Your app is smart but what about compliance? MAD provides support regulatory compliance and a simple way to verify data management security.
|
|
|